[Hacker Zer0]
[Hacker Zer0]
[Cyber Threat Intelligence]
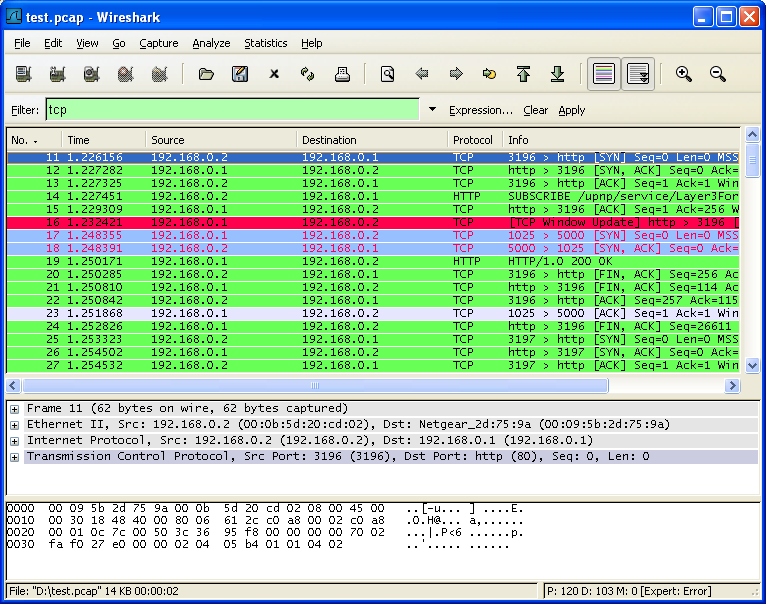
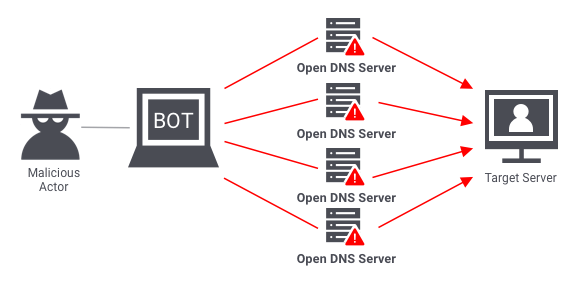
What is Cyber Threat Intelligence Cyber Threat Intelligence is crucial and Important Databases. If you conduct a simple google search for CTI you will be overwhelmed with all of the platforms that are promising to keep your data safe. However I know some amazing links to CTI tools that can help you conduct research and Investigations

These are my Top 8 CTI: Cyber Threat Intelligence
1.UrlScan.io
What it analyzes:
Urlscan.io looks for potential threats and vulnerabilities, such as malicious code, suspicious links, phishing attempts, and other risks. It also checks if the website has been flagged as malicious by other users or security platforms.
2.Cisco Talos
Cisco Talos Intelligence is a Powerhouse of Tools, Vulnerability Research, Incident Response and Security Resources.Such as; Snort, ClamAV, PE-Sig, Synful Knock Scanner, MBR Filter, FIRST, Cisco Smart Install Scanner and so many tools.
3.Abused IP DB
Abuse IP DB is a project dedicated to helping combat the spread of hackers, spammers, and abusive activity on the internet. You can report an IP address associated with malicious activity, or check to see if an IP address has been reported, by using the search box above.
4.Breached Directory
BreachDirectory allows you to search through all public data breaches to make sure your emails, usernames, passwords, and domains haven't been compromised.
5.Checked Leak CC
Check Leaked CC is a is a website that checks for leaked data. They have a free account and a Pro Account. You can research most of your social accounts.
6.Kaspersky Threat MAP
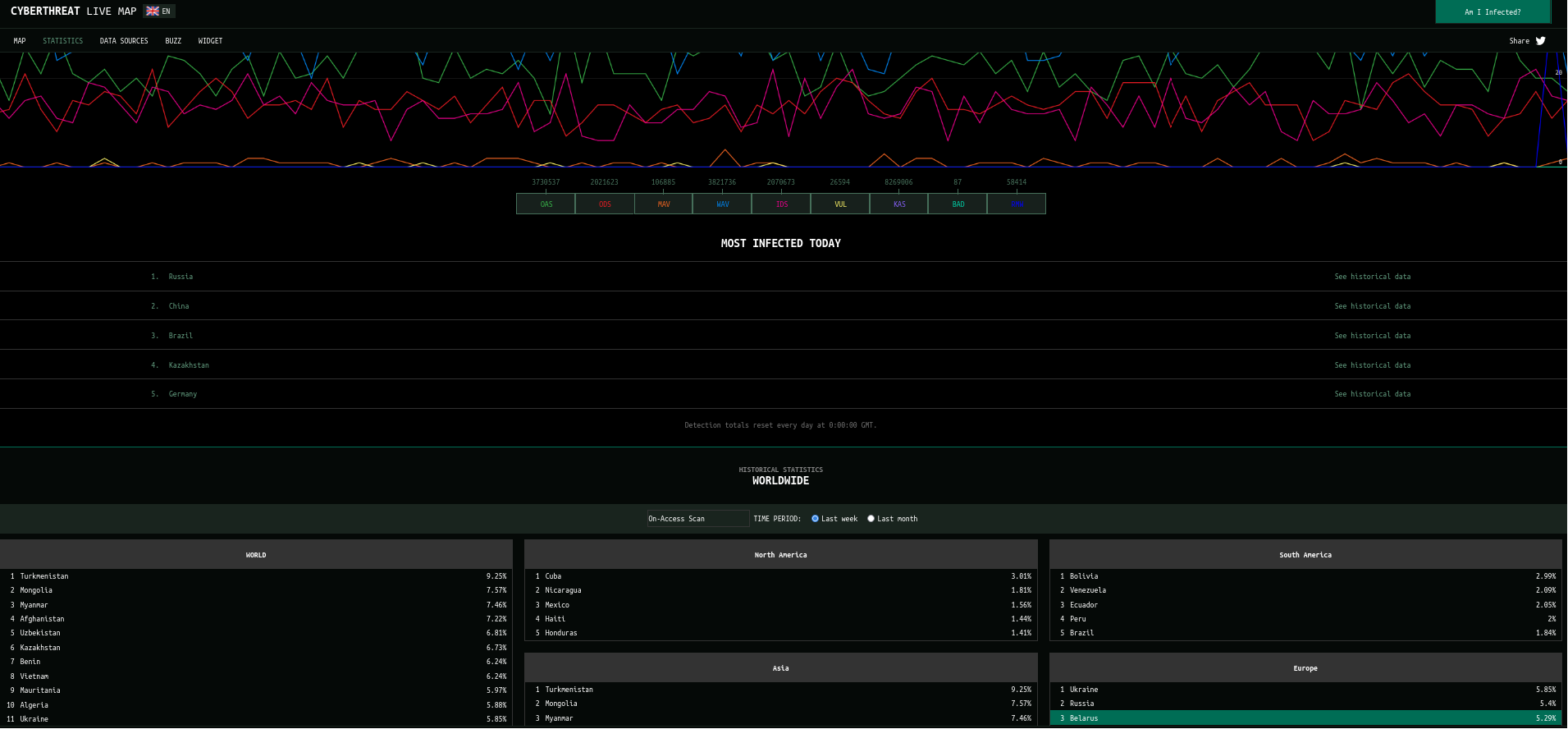
Kaspersky Cyber Threat MAP is the best up-to-date analysis of cyber attacks in real time by country and type of attack.
Kaspersky Digital Footprint Intelligence
A service that helps organizations monitor their digital assets and detect threats from the surface, deep, and dark web. It provides real-time alerts, analytical reports, and the ability to customize monitoring capabilities.
7.Recorded Future
Recorded Future Research: Discover an array of Threat Intelligence Resources at Recorded Future. From in-depth eBooks and enlightening webinars to comprehensive research papers and impactful case studies. Browse through our extensive press mentions and watch testimonial videos to understand how our intelligence solutions empower cybersecurity.
8.Alien Vault

LevelBlue/Labs: with Alien vault's Lab you can find any known vulnerabilities. For example: Users, Groups, Pulses, Malware Families, Adversaries and so much more. The World’s First Truly Open Threat Intelligence Community.Submit files and URLs for free malware analysis within LevelBlue Labs OTX sandbox. Open Threat Exchange is the neighborhood watch of the global intelligence community. It enables private companies, independent security researchers, and government agencies to openly collaborate and share the latest information about emerging threats, attack methods, and malicious actors, promoting greater security across the entire community. The possibilities are endless.